Like the Internet? Get ready to start talking about the way it was in the "Good old days." If the new proposed changes to the principle of network neutrality take hold, the future Internet of classified traffic and preferential speeds threatens to do irreparable damage to the Internet we know and love.
Mozilla has proposed some solutions that are under consideration (or are they?). The Atlantic proposes
we step back and reboot the debate with a fresh look at what's important. And it's gotten more political than ever now, as
Democrats and Republicans have taken sides over the FCC's proposal .
Time for the big companies to say their piece then, too, and they have:
they hate Wheeler's proposal .
Do you care about net neutrality? Do you know the facts? Now is a good time to
make this the next SOPA with the equivalent of a blackout. Look to Brad Feld for a good idea: he proposes we
demo the slowlane , and show Americans exactly what the end of network neutrality means for the average punter's online experience. I think it's an awesome idea.

Is wearable tech the next big thing, or has it already come and gone? Either way, it's the hot topic of 2014.
Blame Google, whose
Google Glass eyewear got everyone excited about something newer and trendier than an expensive smart phone (and made at least some people into instant
glassholes ), or blame Samsung's
Galaxy Gear watch, the
Pebble , and the
Nike Fuelband . It's easy to believe wearable computing is the
next wave of tech innovation. If so, we're not quite there yet, judging by reviews of current products. In fact, some pundits believe innovation is already beginning to
run out of steam .
Wearable tech is being attacked from all angles. While the techies wonder if Google Glass can
pass the ACID test , everyone else is just having enormous amounts of fun
parodying what a family full of wearable computer users might actually look like.

What's the best computer you ever owned? Step aside with your Core Duo, son, and make some room for the gentleman who wants to tell you about his
Commodore 64 . Or
Sinclair ZX . Or
DEC Terminal .
Retro computing is hotter than ever, attracting the interest of a whole new generation who takes interest in the machines of the 60s, 70s, and 80s. You may have missed the
Retro Computing Fair in East Philadelphia last month, but that doesn't mean you're out of luck. Roswell, Georgia is hosting a
Vintage Computing Festival next month, and museums dedicated to classic hardware are springing up everywhere, like
this one in Ramsgate, UK. Most of them are the product of their passionate founders who have opened up their personal collections.
Can't make it anywhere? It's still not too late to
play some classic Commodore 64 games courtesy of a Raspberry Pi and some clever emulation.
That's the thing about bits. Eight of 'em should've been enough for anybody.
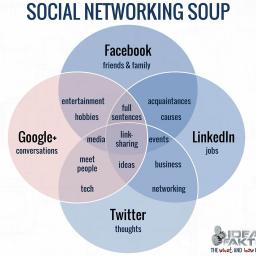
This is either the age of social networking, or it's not. It's either the future, or it's already a has-been. What the heck is going on?
Forbes has printed a thoughtful article on
why Google Plus has failed to thrive . The Atlantic has written a piece suggesting
Twitter is on the decline . Facebook's interest among teens seems to be slowing, while their
"page reach" is down by 50% .
So, what's going on? Is it because, post-
Snowden , everyone is tired of being spied on? Has everyone moved on to cooler platforms? Has everyone ditched social networking and
gone back to Usenet ? Is it possible, as one author suggests, that
privacy is now overtaking sharing on the 'Net? Or has everyone just found something more productive to do, like work in the garden?
[Note: this article has been cross-posted nowhere else. :) Want to comment? Here's the place.]
Video communication, decent but imperfect robots, psychotherapy, self-driving car technology, and processed food: these are some of the things
Isaac Asimov predicted would make up modern life in 2014. The year was 1964, and his vision for 50 years into the future turned out to be surprisingly accurate. A few other predictions fell flat, like underwater colonies or human inhabitation of planets other than earth, but you can forgive the author his exuberance at the dawn of the space age.
The BBC is running an interesting article looking at Asimov's vision and how it played out in real life .
These days,
most teens favor dystopian visions of the future , modern life is
resembling dystopia in more than one way , and the world of peace and unity seems farther off than ever.
Who today has the prescience that Asimov did in 1964? Who among the 21st century's authors, film-makers, and thinkers is most thoughtfully envisioning the world that awaits us in 2064? And what lessons do they provide for us to learn?
Here's a little something to sour your morning coffee with the acid taste of anxiety:
an interesting piece by Joanna Rutkowska pointing out what she claims is an inherent security flaw in the
X Window GUI model :
... Start another terminal window, and switch to root (e.g. using su, or sudo). Notice how the xinput running as user is able to sniff all your keystrokes, including root password (for su), and then all the keystrokes you enter in your root session. Start some GUI app as root, or as different user, again notice how your xinput can sniff all the keystrokes you enter to this other app!
I never knew this and am not aware of much discussion going on about the issue. Is this a fundamental flaw that Windows Vista addresses more successfully, as the author claims, or has the time truly come to do away with the X Window model and develop something else? Did
the UNIX-Haters Handbook get this one right?

What do you get when you cross an enterprising and talented musician with a hardware hacker? For starters, you get Imogen Heap, a UK musician who wants to
change how we interact with our equipment when producing and performing music . She says,
Fifty percent of a performance is racing around between various instruments and bits of technology on stage. I wanted to create something where I could manipulate my computer on the move wirelessly so that music becomes more like a dance rather than a robotic act like pressing a button or moving a fader.
And that's what she's doing. She's
created a pair of technical gloves called Mi.Mu that use a series of sensors to can be connected to standard audio equipment to manipulate sound. Any budding musician that has crouched over his/her digital audio equipment fiddling with knobs, sliders, and faders ought to see the advantage in a new interface that allows you to express your music by moving your body, as well as the potential advantages in a stage performance.
Is this a more interesting future for the coming world of wearable computers and technology? And beyond hands, what can we do with this kind of technology?

So you've just settled into your seat at the movie theater, and as the film starts to roll it begins with an advertisement for the THX Sound System, accompanied by a sound that's
recognizable in a heartbeat, but a bit hard to describe in words [mp3]. That sound is called Deep Note. It was created in 1982 by Dr. James A. Moorer, who used the Audio Signal Processor (ASP), also known as
SoundDroid to create it.
The ASP was a complex machine to program and included about 20,000 lines of C code to program. Only one ASP was ever produced, and LucasFilms LTD owns it. So what do you do if you're an enterprising hacker interested in blowing the covers off your speakers at home by replicating that sound?
You build your own .
Read more at
Hackday.com .
There's more than one way to compute a secure hash, from MD5 to SHA-3 to SHA-1 and beyond. So who cares about yet another: Blake2?
There are a couple of reasons you might be interested in checking out Blake2: It was rated best hash function in the SHA-3 competition, is faster than MD5, and cryptographers find that it's similar to the well-regarded SHA-2 algorithm in ways that matter.
Says developer Zooko Wilcox-O'Hearn:
Jean-Philippe Aumasson, Samuel Neves, Christian Winnerlein, and I decided that what the world needed was not just a secure hash function that was faster than Keccak, but one that was faster than MD5! This is because MD5 (and SHA-1) continue to be very widely used, even in new applications, even though MD5 and SHA-1 are unsafe for many uses. We hypothesized that offering engineers a hash function that was both faster and more secure than their beloved MD5 or SHA-1 might be more effective than haranguing them to upgrade to an alternative that is more secure but slower.
Have a look for yourself at Wilcox-O'Hearn's page.




